Since the 1980s, Mac has been a popular computer platform. However, it is not as easy to find software for Mac computers as it is for PC, because Mac has special requirements. As technology advancements continue to be made, more and more people are turning to Mac as a computer choice.
Not all computer monitoring softwares are available for Mac users, but SniperSpy is. It is the best keylogging software available for Mac. This software has made it easy for parents to allow their children to own a Mac, and still be monitored.
SniperSpy will allow you to gain the knowledge of what is happening on your child or employee’s computer when you are not around. SniperSpy is known as a keylogger software, which captures all keystrokes that are preformed on the keyboard. However, this software is packed full of features that make it a clear choice for monitoring a Mac computer.
Try out the robust features of SniperSpy Mac with the free 7 days trial and see how easy it is to use: http://www.sniperspymac.com/download.html
How it Works
Once you buy the software, you can install it directly or remotely onto the Mac. This in itself is unique, as most computer monitoring softwares require you to download the software directly.
You can rest assure that the monitored user is not engaging in mischievous behavior, which could lead to consequences.
This is a fantastic way for employers to gain the knowledge of what their employees are doing during work hours. Especially if that employee works off site, and has been given a company Mac for work purposes.
Features
SniperSpy is packed full of features, which makes it the most advanced monitoring software in its class. To better understand these features, they have been broken down into categories.
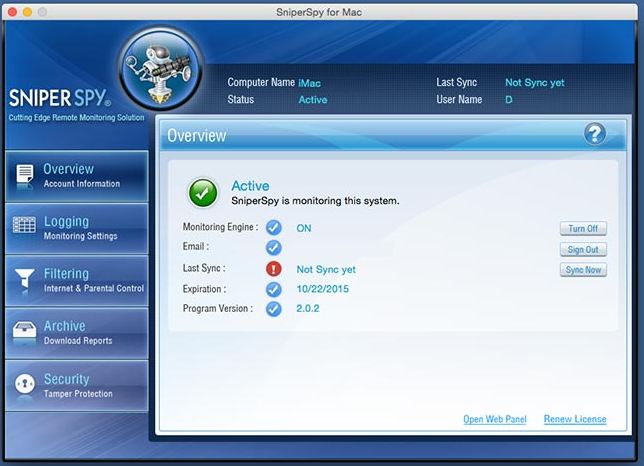
Recorded Activity
These features are the ones that give you the answers you are looking for. Not only will you receive a log of the users activity, you will also be supplied with a jpg image of the users active window. You can set this up to supply the jpg image for as often as you like. This setting can be changed in the online control panel, also known as the viewers account. The great thing is, the image has the ability to be shrunk to your screen, or you can zoom to read text at its full capacity.
Here is a list of the record activity features
- Actual Screenshots: Provides a full sized screen shot of the users active screen.
- Surround Recording: This is one of the newest features for SniperSpy. It conveniently records all audio surrounding the computer by accessing the computer’s microphone. You can pre-set this to record as often as you like, or activate it when you feel it is necessary.
- Websites Visited: Receive a recorded log of all websites the user visited within Safari or Firefox web browsers.
- Keylogger: All keystrokes are recorded and uploaded for you to see.
- Social Media: Monitor popular social media platforms such as Facebook or Myspcae. A detailed log will be uploaded of all activities performed while accessing these platforms.
- Clipboard Logs: Logs all the text that was copied, as well as the program that it was copied from.
- User Activity Logs: View all startups, shutdown, and log on/off times.
- Profanity Alert Logs: Set up this setting to alert you whenever profanity or obscene words are typed in the monitored Mac.
- Locating: From a remote location you can view where the Mac is located on a map.
- Chat Conversations: Log of all instant messengers including Google Talk, Yahoo IM, and Windows Live.
- Applications Executed: See all applications that were accessed on the Mac.
- Duration: Receive details of start and stop times of an application.
- Automatic File Uploads: View all files that were accessed, added, renamed, as well as the path to the file.
- Email Reports: Enter an email address to have activity logs sent straight to you.
Real Time Monitoring
You become the ultimate spy with the help of LIVE surveillance, and the ability to control the Mac from a remote location. You can watch the activity just like you watch a television screen, and you can send commands to the computer instantly. When commands are sent, the software uses the SniperSpy server to act as an intermediary, which allows you to instantly send commands to the monitored Mac.
- LIVE Control allows you to gain knowledge of the Mac user’s activity instantly. This will help you take action right away, when mischievous behavior is detected. This is the most powerful tool any parent or employer could have because it allows you to stop the activity in its tracks.
- LIVE Screen: View the Mac’s surroundings in real time, and watch it just like a television screen.
- LIVE Keystrokes: Watch as each keystroke is being typed.
- Send a Message: Execute a message to the monitored Mac at any time.
- Real Time Webcam Snapshot: Execute a command to record an instant snapshot by using the Mac’s webcam.
- Reboot/Shutdown/Logoff: Send a remote command to shutdown, reboot or log off the Mac.
- File Browser with Search: View all files stored on the Mac from a remote location.
- Hide Desktop Icons: Send a command to hide desktop icons.
- View Bookmarks: View all web browser bookmarks.
- Active Processes: See what processes are actively being used on the Mac, and send a command to stop any of them that you choose.
- Launch an Application or Web Address: From a remote location send a command to launch an application or website.
- Uploaded Files: View files that are uploaded to or downloaded from the monitored MAC.
- View Recent Documents: View documents that have recently been opened.
- Live Events: View programs that are opened, closed or changed as they happen.
Content Filtering Features
With all the users activity being monitored, SniperSpy has made it easy for you to control what is allowed to be done on the monitored device. If there are things you forbid the user to access, you can set up a filter so they will not be allowed to access it from the monitored Mac. By blocking these activities you will receive less logged activities to sift through, because the software will deny access to your blocked commands.
- Application Filter: Set up a block so certain applications cannot be used on the computer.
- Web Filter: Set up a blacklist and whitelists of restricted and allowed websites.
- IM Filter: Choose which chats or IMs can be accessed or blocked.
- Social Media Filter: Block any forbidden social media sites.
- Time Control: Set up a time frame that the user is allowed to access the computer.